
021 837 597
Do you feel Secure?
At Everest Infosec, we will help you scale the peak of Cybersecurity Protection.
Do you feel
Secure?
At Everest Infosec, we will help you scale the peak of cybersecurity protection.
CYBERSECURITY
ROBUST PROTECTION
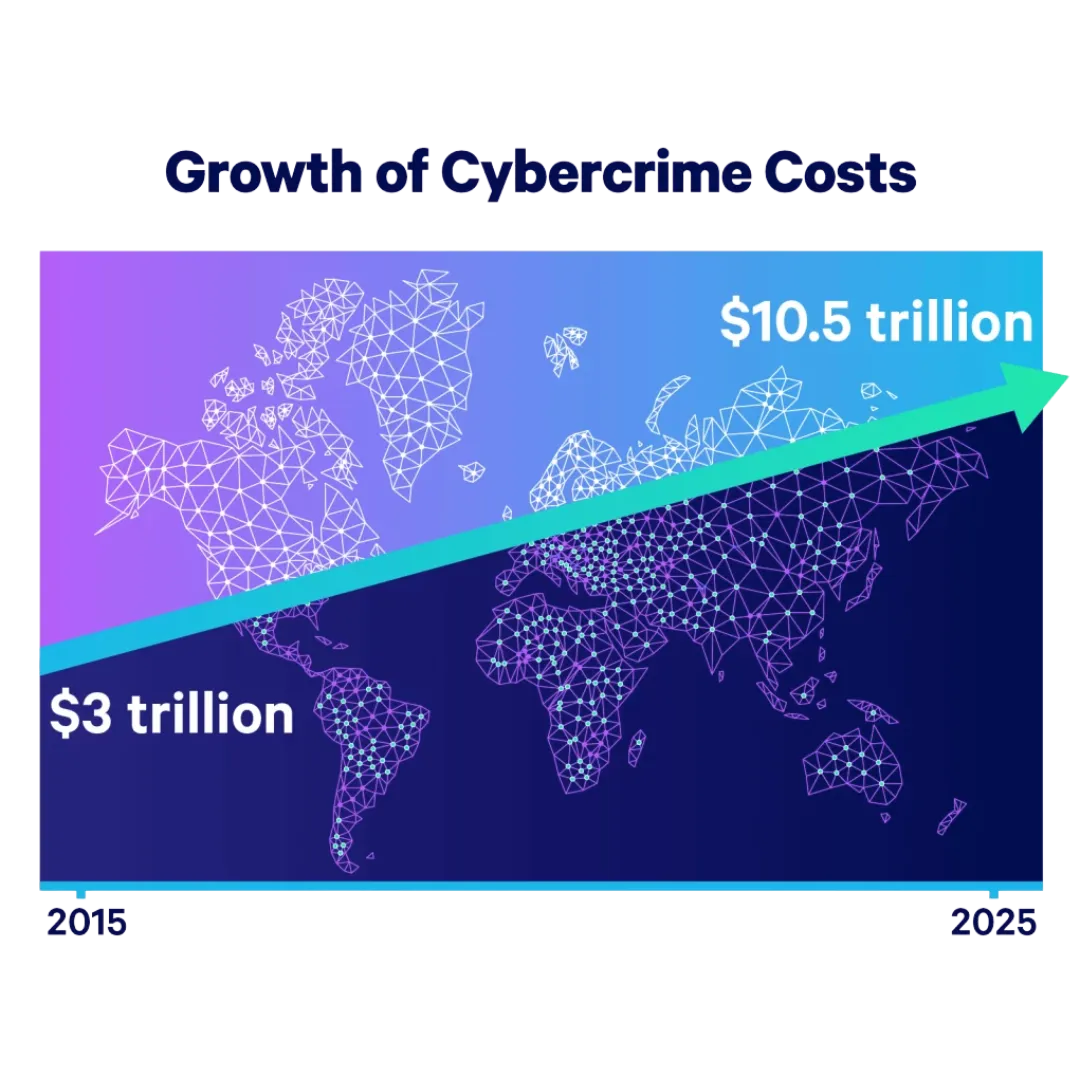
Elevate your defenses as global cybercrime costs soar to $10.5 trillion by 2025 and ransomware now strikes 59 % of organizations—each breach averaging $3.58 million in recovery expenses.
Cyber insurance spend is set to jump from $14 billion in 2023 to $29 billion by 2027, even as a talent shortfall of four million professionals today threatens to swell to 85 million by 2030.
With Generative AI powering ever-smarter phishing, malware, and deepfake attacks, our seasoned CISO and dedicated security team deliver seamless, next-generation defenses tailored to your unique needs.
Services We Provide
Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
Vivamus elementum semper nisi.
Sed consequat leo eget bibendum sodales augue velit.
Maecenas nec odio et ante tincidunt tempus.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus.

Our Services

Security | Posture | Technical | Data Centre Audits | Vulnerability Assessments
We can review your organisation's information systems, policies, and practices to identify vulnerabilities, assess compliance with security standards and regulations, and make recommendations for improving security measures.
We also conduct physical pentests and audits of data centres and other sites, to provide you with actionable insights on security gaps, vulnerabilities, risks and compliance issues.

Consulting and Strategy | Security Awareness and Training
Our experienced consultants can develop and manage your organisation’s projects to enhance cybersecurity measures. This includes assessing current security practices, making recommendations for improvement, quickly establishing security policies and procedures, and creating a strategic roadmap to protect digital assets and mitigate cyber threats.
We are also experienced Business Continuity and Disaster Recovery planners who can help your organization mitigate the effects of unforeseen events, ranging from natural disasters to cyberattacks, and ensure the continuity of business operations.
We can customise programs and activities to educate and inform your staff about security best practices, potential threats, and how to effectively protect sensitive information and digital assets.

Control Mapping | IT Policy Development | IT Service Management | Virtual CISO
Provision of expert advice from experienced
consultants, development of comprehensive plans to help your organization assess, enhance, and effectively manage their cybersecurity measures.
This includes assessing current security practices, making recommendations for improvement, establishing security policies and procedures, and creating a strategic roadmap to protect digital assets and
mitigate cyber threats.

Cyber Forensics
Investigation and analysis of digital evidence, collecting, preserving, and examining digital information to identify the cause, scope, and impact of cyber incidents and to support legal or investigative proceedings.

ISO 27001 Accreditation
Everest Infosec is equipped to help you prepare for ISO 27001 cybersecurity accreditation by providing comprehensive support and guidance throughout the entire certification process.
Our experienced consultants can assist organizations in assessing their current cybersecurity practices, identifying potential risks and vulnerabilities, and implementing effective security measures to meet ISO 27001 standards.
We can offer customized solutions to address each client's unique needs, ensuring that their information security management systems (ISMS) are robust, efficient, and compliant with industry regulations. By partnering with Everest Infosec, you can confidently navigate the complexities of ISO 27001 certification and demonstrate commitment to safeguarding sensitive data and mitigating potential cybersecurity threats.

Portable | Mobile Device Security
Everest Infosec specializes in helping you bolster security on drones, mobile devices, and other portable devices to effectively mitigate cybersecurity risks. By partnering with Everest Infosec, we want to ensure your
valuable data remains protected in the face of evolving threats
by enhancing your security posture, and being able to maintain the integrity of your data resulting from cyberattacks.
Our Services

Security Audit
A systematic evaluation process that examines your organization's information systems, policies, and practices to identify vulnerabilities, assess compliance with security standards and regulations, and make recommendations for improving security measures. We can enhance your organization's cybersecurity posture with services such as penetration and defence testing This will aid in pinpointing weaknesses and vulnerabilities, and ensuring appropriate security controls are in place.

Cloud Security
We will assess your organization's cloud environment safety, design security, and effectiveness of controls.

Consulting and Strategy
Provision of expert advice from experienced
consultants, development of comprehensive plans to help your organization assess, enhance, and effectively manage their cybersecurity measures. This includes assessing current security practices, making recommendations for improvement, establishing security policies and procedures, and creating a strategic roadmap to protect digital assets and
mitigate cyber threats.

IT Policy Development
Creating a set of documented guidelines, rules, and procedures that govern how information technology resources and systems should be used, maintained and secured within your organization. These policies help ensure the consistent and secure operation of IT assets, protect sensitive data, and mitigate cybersecurity risks.

Control Mapping
Aligning and mapping various security control standards so your organization's security practices meet your requirements, progress your compliance journey, and enhance cybersecurity.

Security Awareness and Training
Customizing programs and activities to educate and inform your staff about security best practices, potential threats, and how to effectively protect sensitive information and digital assets.

Technical Security Audits
Systematic examinations of your organization's technical infrastructure, including networks, systems, and software, to assess their security controls, vulnerabilities, and compliance with security standards. These audits aim to identify
weaknesses, potential threats, and areas for improvement in your organization's technical
security measures.

Cyber Forensics
Investigation and analysis of digital evidence, collecting, preserving, and examining digital information to identify the cause, scope, and impact of cyber incidents and to support legal or investigative proceedings.

Email Security Audits
Assessment and evaluation of your organization's email systems, policies, and practices to identify vulnerabilities, risks, and compliance with security
standards.

Virtual CISO (Chief Information Security Officer)
An external or part-time cybersecurity
expert who provides strategic leadership and guidance to organizations in managing their
cybersecurity efforts. We offer you our expertise in developing and implementing security strategies, policies, and controls.

ITSM (IT Service Management)
A set of practices and processes aimed at efficiently delivering and managing IT services within an organization. While it primarily focuses on IT service delivery, ITSM also includes aspects related to managing and responding to cybersecurity incidents within the broader IT service framework.

Business Continuity and Disaster Recovery
Practices that ensure an organization's
ability to maintain essential operations ad recover from disruptions or disasters. Together, BC and DR plans help your organization mitigate the effects of unforeseen events, ranging from natural disasters to cyberattacks, and ensure the continuity of business operations.

ISO 27001 Accreditation
Preparing for ISO 27001 accreditation in cybersecurity takes time, work and money, but our experienced consultants can make the process certification under ISO 27001 as quick and painless as possible.

Security Device Management
We configure, monitor and maintain security devices and tools, such as firewalls, intrusion detection systems, antivirus software, and encryption solutions.

Risk Advisory
Providing expert guidance and recommendations to organization regarding
the identification, assessment, and management of cybersecurity risks. It helps your organization make informed decisions to mitigate risks, improve your security posture, and protect their digital assets and sensitive information. Risk advisory services include risk assessments, business impact assessment, threat modelling, vulnerability assessments, and risk mitigation strategies.

Risk Advisory
Providing expert guidance and recommendations to organization regarding
the identification, assessment, and management of cybersecurity risks. It helps your organization make informed decisions to mitigate risks, improve your security posture, and protect their digital assets and sensitive information. Risk advisory services include risk assessments, business impact assessment, threat modelling, vulnerability assessments, and risk mitigation strategies.

Vulnerability Assessment
Evaluation of your organization's computer systems, networks, and applications to identify and prioritize potential security weaknesses or vulnerabilities. The assessment aims to provide insights into areas where your organization may be
susceptible to cyberattacks or breaches, helping them take proactive steps to address these vulnerabilities before they can be exploited by malicious actors.

Data Centre Audits
A comprehensive examination of your organization's data center facilities, infrastructure, and operations to assess and ensure the security, reliability, and compliance of data storage, processing, and management practices. These audits aim to
identify vulnerabilities, assess adherence to data center standards, and recommend
improvements to enhance data center security and efficiency.

Mobile Device Security
Practices, measures, and technologies implemented to protect smartphones, tablets, and other mobile devices from security threats, such as malware,
unauthorized access, data breaches, and privacy violations. It involves securing both the device hardware and the data and applications it contains, ensuring the safe use of mobile technology in a corporate or personal context.

24/7 SOC Surveillance
Security Operations Centre surveillance by continuous monitoring and analysis of your organization's IT infrastructure, networks, and systems by a dedicated team of security professionals around the clock. The goal is to detect, investigate, and respond to security incidents and threats in real-time to protect against cyberattacks and ensure the security of digital assets and data.

Gap Analysis of Business
evaluating and identifying disparities or "gaps" between your organization's current cybersecurity practices and its desired security goals or industry best practices. The analysis helps your organization understand where their security measures may fall short, enabling them to prioritize improvements and align their security efforts with their business objectives.

Business Maturity Assessment
A comprehensive evaluation of your organization's cybersecurity maturity level. This assessment measures your organization's readiness, capabilities, and effectiveness in managing and mitigating cybersecurity risks. It helps organizations understand their current cybersecurity posture, identify areas for improvement, and develop a roadmap for enhancing their overall cybersecurity maturity.

Security | Posture | Technical | Data Centre Audits | Vulnerability Assessments
We can review your organisation's information systems, policies, and practices to identify vulnerabilities, assess compliance with security standards and regulations, and make recommendations for improving security measures.
We also conduct physical pentests and audits of data centres and other sites, to provide you with actionable insights on security gaps, vulnerabilities, risks and compliance issues.

Consulting and Strategy | Security Awareness and Training
Our experienced consultants can develop and manage your organisation’s projects to enhance cybersecurity measures. This includes assessing current security practices, making recommendations for improvement, quickly establishing security policies and procedures, and creating a strategic roadmap to protect digital assets and mitigate cyber threats.
We are also experienced Business Continuity and Disaster Recovery planners who can help your organization mitigate the effects of unforeseen events, ranging from natural disasters to cyberattacks, and ensure the continuity of business operations.
We can customise programs and activities to educate and inform your staff about security best practices, potential threats, and how to effectively protect sensitive information and digital assets.

Control Mapping | IT Policy Development | IT Service Management | Virtual CISO
Provision of expert advice from experienced
consultants, development of comprehensive plans to help your organization assess, enhance, and effectively manage their cybersecurity measures.
This includes assessing current security practices, making recommendations for improvement, establishing security policies and procedures, and creating a strategic roadmap to protect digital assets and mitigate cyber threats.

Cyber Forensics
Investigation and analysis of digital evidence, collecting, preserving, and examining digital information to identify the cause, scope, and impact of cyber incidents and to support legal or investigative proceedings. Weaknesses, potential threats, and areas for improvement in your organization's technical security measures.

ISO 27001 Accreditation
Everest Infosec is equipped to help you prepare for ISO 27001 cybersecurity accreditation by providing comprehensive support and guidance throughout the entire certification process.
Our experienced consultants can assist
organizations in assessing their current cybersecurity practices, identifying potential risks and vulnerabilities, and implementing effective security measures to meet ISO 27001 standards.
We can offer customized solutions to address each client's unique needs, ensuring that their information security management systems (ISMS) are robust, efficient, and compliant with industry regulations. By partnering with Everest Infosec, you can confidently navigate the complexities of ISO 27001 certification and demonstrate commitment to safeguarding sensitive data and mitigating potential cybersecurity threats.

Portable | Mobile Device Security
Everest Infosec specializes in helping you bolster security on drones, mobile devices, and other portable devices to effectively mitigate cybersecurity risks. By partnering with Everest Infosec, we want to ensure your valuable data remains protected in the face of evolving threats
by enhancing your security posture, and being able to maintain the integrity of your data resulting from cyberattacks.
Our Services

Security Audit
A systematic evaluation process that examines your organization's information systems, policies, and practices to identify vulnerabilities, assess compliance with security standards and regulations, and make recommendations for improving security measures. We can enhance your organization's cybersecurity posture with services such as penetration and defence testing This will aid in pinpointing weaknesses and vulnerabilities, and ensuring appropriate security controls are in place.

Cloud Security
We will assess your organization's cloud environment safety, design security, and effectiveness of controls.

Consulting and Strategy
Provision of expert advice from experienced
consultants, development of comprehensive plans to help your organization assess, enhance, and effectively manage their cybersecurity measures. This includes assessing current security practices, making recommendations for improvement, establishing security policies and procedures, and creating a strategic roadmap to protect digital assets and mitigate cyber threats.

IT Policy Development
Creating a set of documented guidelines, rules, and procedures that govern how information technology resources and systems should be used, maintained and secured within your organization. These policies help ensure the consistent and secure operation of IT assets, protect sensitive data, and mitigate cybersecurity risks.

Control Mapping
Aligning and mapping various security control standards so your organization's security practices meet your requirements, progress your compliance journey, and enhance cybersecurity.

Security Awareness and Training
Customizing programs and activities to educate and inform your staff about security best practices, potential threats, and how to effectively protect sensitive information and digital assets.

Technical Security Audits
Systematic examinations of your organization's technical infrastructure, including networks, systems, and software, to assess their security controls, vulnerabilities, and compliance with security standards. These audits aim to identify
weaknesses, potential threats, and areas for improvement in your organization's technical
security measures.

Cyber Forensics
Investigation and analysis of digital evidence, collecting, preserving, and examining digital information to identify the cause, scope, and impact of cyber incidents and to support legal or investigative proceedings.

Email Security Audits
Assessment and evaluation of your organization's email systems, policies, and practices to identify vulnerabilities, risks, and compliance with security
standards.

Virtual CISO (Chief Information Security Officer)
An external or part-time cybersecurity
expert who provides strategic leadership and guidance to organizations in managing their
cybersecurity efforts. We offer you our expertise in developing and implementing security strategies, policies, and controls.

ITSM (IT Service Management)
A set of practices and processes aimed at efficiently delivering and managing IT services within an organization. While it primarily focuses on IT service delivery, ITSM also includes aspects related to managing and responding to cybersecurity incidents within the broader IT service framework.

Business Continuity and Disaster Recovery
Practices that ensure an organization's
ability to maintain essential operations ad recover from disruptions or disasters. Together, BC and DR plans help your organization mitigate the effects of unforeseen events, ranging from natural disasters to cyberattacks, and ensure the continuity of business operations.

ISO 27001 Accreditation
Preparing for ISO 27001 accreditation in cybersecurity takes time, work and money, but our experienced consultants can make the process certification under ISO 27001 as quick and painless as possible.

Security Device Management
We configure, monitor and maintain security devices and tools, such as firewalls, intrusion detection systems, antivirus software, and encryption solutions.

Risk Advisory
Providing expert guidance and recommendations to organization regarding
the identification, assessment, and management of cybersecurity risks. It helps your organization make informed decisions to mitigate risks, improve your security posture, and protect their digital assets and sensitive information. Risk advisory services include risk assessments, business impact assessment, threat modelling, vulnerability assessments, and risk mitigation strategies.

Risk Advisory
Providing expert guidance and recommendations to organization regarding
the identification, assessment, and management of cybersecurity risks. It helps your organization make informed decisions to mitigate risks, improve your security posture, and protect their digital assets and sensitive information. Risk advisory services include risk assessments, business impact assessment, threat modelling, vulnerability assessments, and risk mitigation strategies.

Vulnerability Assessment
Evaluation of your organization's computer systems, networks, and applications to identify and prioritize potential security weaknesses or vulnerabilities. The assessment aims to provide insights into areas where your organization may be susceptible to cyberattacks or breaches, helping them take proactive steps to address these vulnerabilities before they can be exploited by malicious actors.

Data Centre Audits
A comprehensive examination of your organization's data center facilities, infrastructure, and operations to assess and ensure the security, reliability, and compliance of data storage, processing, and management practices. These audits aim to identify vulnerabilities, assess adherence to data center standards, and recommend improvements to enhance data center security and efficiency.

Mobile Device Security
Practices, measures, and technologies implemented to protect smartphones, tablets, and other mobile devices from security threats, such as malware, unauthorized access, data breaches, and privacy violations. It involves securing both the device hardware and the data and applications it contains, ensuring the safe use of mobile technology in a corporate or personal context.

24/7 SOC Surveillance
Security Operations Centre surveillance by continuous monitoring and analysis of your organization's IT infrastructure, networks, and systems by a dedicated team of security professionals around the clock. The goal is to detect, investigate, and respond to security incidents and threats in real-time to protect against cyberattacks and ensure the security of digital assets and data.

Gap Analysis of Business
evaluating and identifying disparities or "gaps" between your organization's current cybersecurity practices and its desired security goals or industry best practices. The analysis helps your organization understand where their security measures may fall short, enabling them to prioritize improvements and align their security efforts with their business objectives.

Business Maturity Assessment
A comprehensive evaluation of your organization's cybersecurity maturity level. This assessment measures your organization's readiness, capabilities, and effectiveness in managing and mitigating cybersecurity risks. It helps organizations understand their current cybersecurity posture, identify areas for improvement, and develop a roadmap for enhancing their overall cybersecurity maturity.
About Everest Infosec
We lead the way in providing outstanding cybersecurity defence and credential solutions from small businesses to large enterprise platforms.
Our team of experts will take a real world approach to delivering comprehensive, adaptable solutions to improve your cybersecurity.


About Everest Infosec
We lead the way in providing outstanding cybersecurity defence and credential solutions from small businesses to large enterprise platforms.
Our team of experts will take a real world approach to delivering comprehensive, adaptable solutions to improve your cybersecurity.
Our Mission
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor.
Our Philosophy
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa.
Our Promise
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa.
Our Guarantee
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa.
Our Blogs
No blogs found
Frequently Asked Questions
Q:
Lorem ipsum dolor sit amet, consetetu sadipscing elitr, sed diam nonumy!
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est.
Q:
Lorem ipsum dolor sit amet, consetetu sadipscing elitr, sed diam nonumy!
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est.
Q:
Lorem ipsum dolor sit amet, consetetu sadipscing elitr, sed diam nonumy!
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est.
Q:
Lorem ipsum dolor sit amet, consetetu sadipscing elitr, sed diam nonumy!
Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est.

© Copyright 2025. Everest Infosec. All rights reserved.
Follow Us
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium!
Services
More
Contact Us
021 837 597
Ksenia Drive
- Monday - Friday, 8:00 am - 5:00 pm

